
Wi-Fi Roaming
Connect to Wi-Fi Anywhere-Effortlessly
Mobile users flock to Wi-Fi as soon as they can, rushing to an open Wi-Fi network like it's an oasis in the desert. But they usually have to work for it: finding and selecting the right network, logging on through a portal, often having to re-enter their credentials multiple times. So while public Wi-Fi services are growing by leaps and bounds, they're still a pain for users. Which means that operators deploying it aren't seeing as much usage-and value-as they otherwise might.
Wouldn't it be nice if Wi-Fi could work like cellular roaming-if users could just power up their device, and they'd be online? With the 802.11u wireless roaming standard and Hotspot 2.0, now they can.
Keep Your Customers Connected
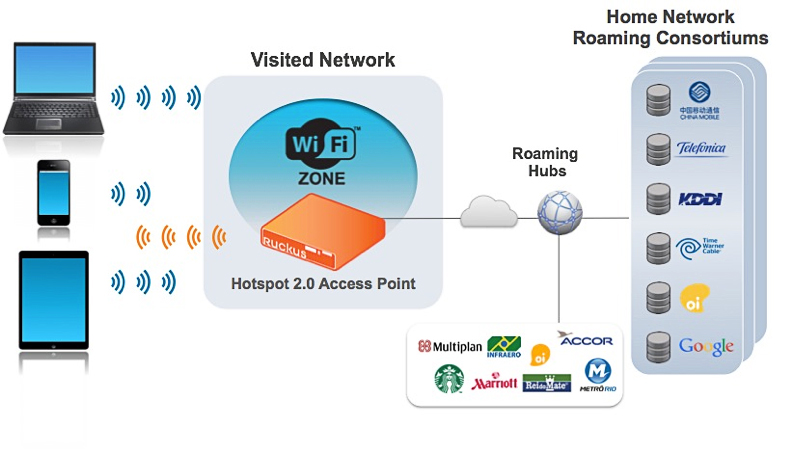
Hotspot 2.0 makes public Wi-Fi as simple and seamless for subscribers as cellular roaming. Just as their cell phone automatically finds a roaming partner network and securely connects no matter where they are, users can get the same experience over Wi-Fi.
Whether you're a mobile operator, cable provider or anyone else offering public Wi-Fi, you can enter roaming partnerships with other providers to make Wi-Fi connectivity seamless for your customers-across the country and around the world. Which means more revenue opportunities, more ways to stay connected with customers, and happier subscribers.
Secure Connections Made Simple
With Hotspot 2.0, operators and their subscribers load devices with the right credentials and security certificates-either beforehand or in real-time, when users are near a participating network. Then, anytime users are away from the home network provider, their devices automatically check for Hotspot 2.0-capable networks from participating roaming partners. If one is available, users connect automatically, without doing a thing.
Wi-Fi providers have a range of options for connecting subscriber devices-digital certificates, usernames and passwords, SIM- or non-SIM based credentials. They can use Public Key Infrastructure (PKI) to authenticate and encrypt connections. And they can tightly control policy on when, where and how subscribers take advantage of the service.

